For a Viz Data Connectors dataset to work correctly, an existing account with Flowics by Vizrt must be obtained (separately) by the customer. Additionally, the connectors to forward to Datacenter via the Flowics Middleware, as well as its setup, must be performed via the Flowics web-ui. Please refer to the Flowics by Vizrt documentation for further information on how to install the Fowics Middleware.
Note: The Viz Data Connectors integration requires Datacenter to run in HTTPS mode. Please refer to the General Configuration page for instructions on how to setup a HTTPS service.
This section provides the steps to configure a Viz Data Connectors dataset using Flowics Middleware.
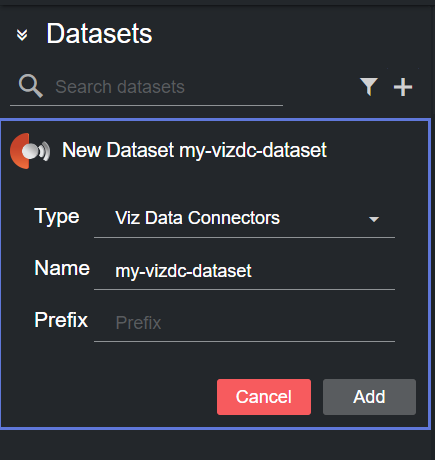
Create a new dataset of type Viz Data Connectors, specifying a name and (optionally) a prefix to use to identify the dataset and its values:
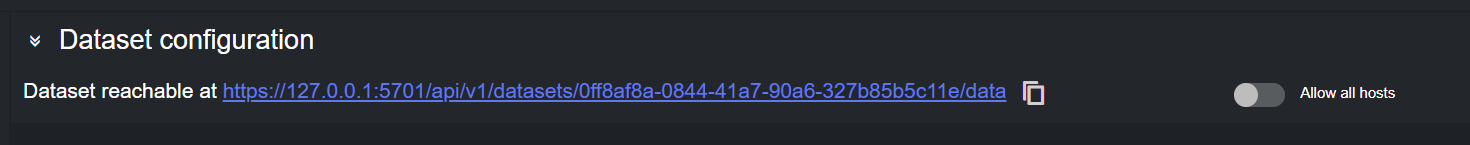
Click Add. The following link is displayed in the Dataset configuration panel:
This link can be used in the Flowics web-ui, to configure the Middleware to forward data to Datacenter.
The basic setup assumes that both Datacenter and the Flowics Middleware run on the same machine. When this is the case, no further steps are required to setup a Flowics dataset, and any data configured to be forwarded by the Middleware, should also appear in the Dataset Entries panel. However, for setups where Datacenter runs on a different machine than the Flowics Middleware, the following additional steps have to be performed:
In Datacenter's Dataset configuration panel, enable the Allow all hosts toggle.
Substitute the localhost/127.0.0.1 part of the address shown in the Dataset configuration panel with the machine public IP, and use this new address to configure the Middleware to forward data to Datacenter.
Info: On Windows, a machine IP can be found by running the ipconfig command from a command line terminal (CMD), or the Get-NetIPAddress cmdlet in Powershell.
Please refer to the Filtering and Manipulating a Dataset Entries page to learn how to enable, disable and edit the entries added.
Configuring Middleware to Send Data to Datacenter
Note: This guide assumes the Flowics Middleware has been installed on a machine in the following location: /home/user/dev/middleware-cli. Please refer to the Flowics by Vizrt documentation for further information on how to install the Fowics Middleware.
Middleware Token
Note: The token used when configuring Middleware can be found in the Flowics web-ui, under Settings → Middleware → General Settings → Token. This value needs to be associated to the entry flowics.middleware.id in the file middleware.properties, found in /home/user/dev/middleware-cli/conf.
The Middleware can be accessed via the Flowics platform. For that, a registered user account is required.
To start sending data to Datacenter:
Once logged in, navigate to Data Connectors → Data Middleware Sources and select the source from the list where relaying to Datacenter needs to be enabled.
On the Data Source page, locate the Middleware Integration section and click on the Edit button. In the dialog that opens, make sure to enable Push to an HTTP Webhook and in the Endpoint input the Datacenter dataset link shown in the Dataset configuration panel.
Info: If the Middleware runs on a separate machine than the one running Datacenter, substitute the localhost/127.0.0.1 part of the address in the Dataset configuration panel, with the machine public IP.
Click Save. The configuration should be downloaded to the Middleware, and shortly after the dataflow should start towards Datacenter.
Using Signed Certificates
Note: Please refer to the General Configuration page for instruction on how to setup Datacenter to run as an HTTPS service.
The Flowics Middleware requires Datacenter to run an HTTPS service to correctly forward data to it. Please note that Datacenter does not provide signed certificates. Should you not already have a certificate-authority provided certificate, there are several services that can issue signed certificates (for example, letsencrypt.org). When using a TLS certificate signed by a valid authority, no further steps are required to integrate Middleware to Datacenter (this is the recommended way to integrate both).
Using Self-Signed Certificates
Editing a Trust Store
Warning: The following guide requires you to edit the Java Virtual Machine (JVM) trust store. This can potentially expose your machine to malicious actors and attacks, therefore, we recommend carrying the following steps with care. Please have your IT team assist you during this process.
In case you are not able to obtain a certificate-authority provided certificate, a self-signed certificate can be used to run Datacenter as an HTTPS service. This, however, is not the recommended way to setup Datacenter in HTTPS mode, and should only be done under the supervision of your IT team and following an informed decision to use self-signed certificates.
While self-signed certificates are easy to obtain, they do not provide any trust value, and are therefore rejected by default by many communicating actors, including Flowics Middleware. To allow the Middleware to accept self-signed certificates from Datacenter, some additional work is required.
Note: Please refer to the General Configuration page for instructions on how to create a self-signed certificate.
Info: This guide assumes the JVM used to run Middleware is installed in /home/user/jre-21, while Flowics Middleware is installed in /home/user/dev/middleware-cli.
To enable Middleware to accept self-signed certificates, one needs to ensure that:
The self-signed certificate is imported in the Java Virtual Machine (JVM) trust store.
We strongly recommend to first create a copy of the default JVM trust store, and add the self-signed certificate to the copy only. This prevents making permanent changes to the machine's trust store
Warning: Avoid changing the default JVM trust store, instead, work on a copy. We strongly recommend to carry out this step only under the supervision of your IT team.
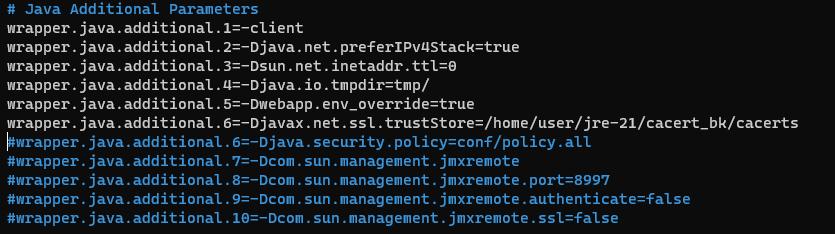
If a copy of the JVM trust store has been used (for example, in /home/user/jre-21/cacert_bk/cacerts), Middleware needs to be made aware of its location. This can be done by adding a line pointing to the modified trust store in the config file /home/user/dev/middleware-cli /conf/middleware.conf. To do so, open this config file and replace the line starting with wrapper.java.additional.6 with the following line:
wrapper.java.additional.6=-Djavax.net.ssl.trustStore=/home/user/jre-21/cacert_bk/cacertsCreate an alias for the IP address of the machine running Datacenter by opening the operating system hostfile /etc/hosts file and adding the line (assuming Datacenter runs at 1.2.3.4:5701):
1.2.3.4 YOUR_DATACENTER_HOST_NAME
Note: The YOUR_DATACENTER_HOST_NAME value, must match the CN field listed in the self-signed certificate used on the Datacenter machine.
Info: Typically, the hostfile in the Windows installation can be located under C:\windows\system32\drivers\etc, while in Linux, the same file can be found in /etc/hosts.
Warning: We strongly recommend to carry out this step only under the supervision of your IT team.
Finally, restart Middleware.